Recently during a consulting engagement with a Fortune 100 client and again during a Design Jam with IFTF (Institute For the Future), I’ve had the opportunity to teach others a bit about cryptography, blockchains and the Metacurrency Project.
Here is an outline of some of the building blocks that I’ve
walked people through as of late. This is a quick first swipe and could probably use some cleanup. Please comment with suggestions about places I’ve gone wrong or things that could be spelled out more clearly.
Kudos to Arthur Brock, Eric Harris-Braun, Christopher Allen, Harlan Wood, Jack Senechal, Travis Wellman, Jorge Lopez, Bruce Schneier and Wikipedia.
===
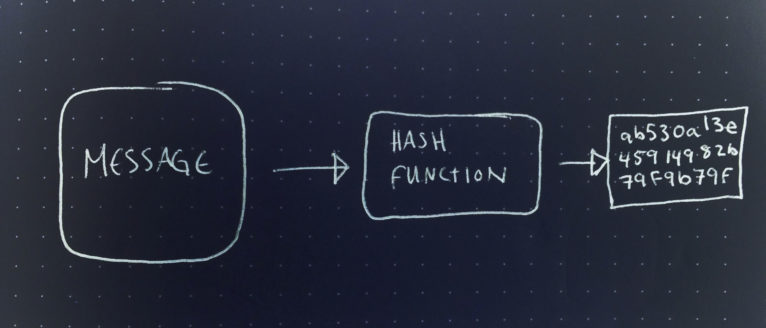
Cryptographic Hash Function: A function which takes an input (or ‘message’) and returns a fixed-size alphanumeric string, called the hash value or digital fingerprint.
Should be:
1) Extremely easy to calculate a hash for any given data.
2) Extremely computationally difficult to determine an input message that will generate a specific hash.
3) Extremely unlikely that two even slightly different messages will have the same hash. (this would constitute a “collision”).
Hash Chain: A data structure which uses successive applications of a hash function. When you use hash chains for non-repudiation, you apply a hash function successively to additional pieces of data to record their chronology. Each successive entry is linked to the previous entry by integrating its hash. If data is altered anywhere in the sequence, it disrupts all of the following hashes, exposing any tampering.
Public Key Cryptography: A user generates a set of asymmetrical keys using specific mathematical functions. One is a public key, the other a private key. You can use one key to encrypt data using asymmetric encryption methods such as RSA, which can then only be decrypted with the other key.
Cryptographic Signatures: A cryptographic signature is typically generated by encrypting a hash of the data you wish to sign using public/private key encryption. These signatures are usually used for:
Authentication – confirming it was sent from a person holding the private key
Non-Repudiation – ensuring you can’t deny having sent/signed it
Validating Data Integrity – ensuring nobody can tamper with the data without breaking your signature
Blockchains: mechanism for enabling a group of participants to create, maintain and leverage a shared, distributed ledger. This enables individuals to make use of trustable digital records to build new ways of coordinating with one another.
Semantic Trees: Storing data with a semantic marker linked to the original definition of how it is used, gives other agents (whether human or computer) clear context and meaning for the data. This enables a process by which the two parties can “generate shared context” through a back and forth iterative communication dance – and thus pivot their way toward “shared meaning.” This (imperfect) overlap in meaning can become “good enough” to enable the participants to coordinate with one another. Semantic Trees are a core component of the Metacurrency Project.
Self-Describing Interoperable Protocols: Protocols are agreed upon rules for interaction (or communication). If you structure a message in accordance with the guidelines included in a particular protocol anyone that is conforming to the protocol can receive that message and make sense of it. Today, protocols are human written documents. And they require both the sender and the receiver to use humans to conform their creation of software to fit the human written protocol. This creates friction when trying to get users of one protocol to be able to communicate with others than don’t yet use that protocol. With self-describing interoperable protocols, a machine can receive a message, not have the protocol for interpreting that message, look it up, install it (in context) and then interpret the message and begin interacting with the sender. This enables new more automated forms of communication and processing – and may lead to new forms of coordination amongst individuals and communities. However, it may not be possible without something akin to Semantic Trees.
Blockchains: using some of the above cryptographic tools as well as either
1) game theory mechanisms (permissionless blockchains) or
2) reputation (permissioned blockchains) or
3) both
the participants in a network are able to ensure the integrity of records without having to restrict access to those records. Even though all users have access to the records, they are not necessarily able to make sense of all records. This is due to some records being stored in an encrypted form and only certain participants having access to the appropriate decryption key(s). Together these enable new forms of coordination. Blockchains in particular enable the participants to share a history – and it is a history as perceived from a single point of view (the perspective of the network as a whole).
Holochains (Metacurrency’s term, but Agoric seems to make use of a very similar concept): by having the participants in an interaction countersign one another’s hash chain’s, we can create an immutable (unchangeable) record of the interaction. This allows each participant to maintain a record of their state AND it creates a separate record that the other party (or others that interact with them) can use to prove that the interaction occurred. These immutable records are useful in a variety of ways, including as evidence to enable reputation pressures to discourage dishonest behavior of actors. Mimicking nature (and unlike typical blockchains) each actor does not have to keep track of every event in the system. This is a big efficiency gain. In addition, different actors are able to view “the system” from different vantage points and this diversity of vantage points actually increases the resilience of the system as a whole.

Leave a Reply